On July 18, 2021, an investigative report led by Forbidden Stories and Amnesty International was published after a list containing 50,000 phone numbers of potential government surveillance targets was leaked to the Forbidden Stories team. The list is linked to the Pegasus Spyware created by the Israeli NSO group. Founded in 2010 by Niv Carmi, Shalev Hulio, and Omri Lavie, the NSO group produced the Pegasus Spyware in an effort to:
“[…] save lives, help governments around the world prevent terror attacks, break up pedophilia, sex, and drug-trafficking rings, locate missing and kidnapped children, locate survivors trapped under collapsed buildings, and protect airspace against disruptive penetration by dangerous drones.”
Current scope of the investigation
The NSO recently published a statement denying all claims and announcing an immediate investigation on all NSO partners and clients. But the list of 50,000 smartphone numbers leaked a few weeks ago – including phones belonging to priests, victims of state-sponsored crimes, and the children of high-profile figures – severely undermined NSO’s claims that its hacking software is only used by its clients to fight serious crime and terrorism.
A total of 180 journalists hailing from 20 plus countries have been identified as targets as of July 18, 2021. With tools provided to us by Amnesty’s tech team, our tech team has identified targets from Eritrea and Ethiopia, adding to the growing list of infected users captured on the Digital Violence website (skip the graphics to see their list of compiled targets). Their website displays a three-dimensional, interactive graph of thousands of events triggered by Pegasus:
- Murder – incidents of fatal violence or assassination.
- Assault – instances of physical violence.
- Intimidation – instances of violence aimed at causing fear and emotional and psychological distress.
- Black Cube – incidents where agents from private Israeli investigation firm Black Cube reportedly intimidate or seek to covertly illicit damaging information about investigators, lawyers, and journalists reporting on NSO related operations.
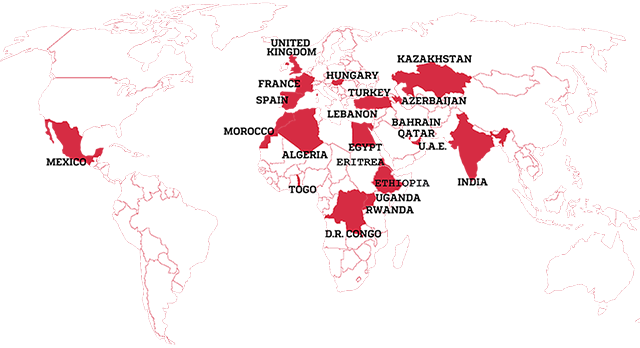
Countries found using spyware against their dissidents
Recent stories linked to Pegasus

Probably the most prominent attack so far was the Jamal Khashoggi killing. Saudi Arabia, using Pegasus, hacked the phones of Jamal Khashoggi’s ex-wife and his fiancee and used the information to prepare the murder and subsequent cover-up. The intel obtained by the Pegasus hack was used to lure Khashoggi into the Saudi consulate in Istanbul on the pretext of providing his papers for his upcoming wedding. It was reported that Khashoggi was ambushed, suffocated, and dismembered by a squad of Saudi assassins.
Khashoggi, for decades, was close to the Saudi royal family and also served as an adviser to the government. However, he fell out of favor with the crown prince. He went into a self-imposed exile in the US in 2017 after his Al-Arab News Channel was shut down for airing an interview with a prominent local opposition activist. His efforts to expose the Saudi government continued as a journalist for the Washington Post. His efforts there eventually led to his assassination.
Khashoggi’s death is just one example of Pegasus’s use to attack investigators:
- 2013 – Ex-Spy Chief David Batenga’s uncle Patrick Karageya, the former Rwandan intelligence chief and founder of the RNC, was found murdered in a South African hotel room.
- 2019 – Human rights advocate Frank Ntwali sees part of private conversations he had while in South Africa appearing in Pro-government Rwandan newspapers.
- 2020 – A series of articles are published online attacking Amnesty’s exposures of the use of NSO to attack Omar Radi.
Eritrea and Ethiopia’s Government

Today, more than ever, Isaias Afwerki and Eritrea’s government have been examined under a critical eye for their involvement in the genocide against Tigray. Just two days ago, UNICEF reported that more than 100,000 children in the Tigray region could die of hunger as many of the roads and bridges used for aid support have either been blocked or destroyed by Ethiopian and Eritrean soldiers.
Many Eritrean and Ethiopian human rights advocates, investigative journalists, and activists have taken a stand against the actions of their governments by coordinating global protests, appearing on news channels, and raising awareness on the issues both governments have tried to conceal. Abiy Ahmed, prime minister of Ethiopia, has completely blacked out communications in the Tigray region since the start of the armed struggle.
On July 29, Access Now, a nonprofit news organization advocating for the stoppage of telecommunication shutdowns in authoritarian countries worldwide published their findings on Ethiopia from 2016 shutdowns in Oromia to present-day shutdowns in Tigray.
The Eritrean government purposefully suppresses its citizens by denying them access to the world wide web. Eritrea is ranked as one of the worst countries in the world for internet penetration, with less than 2% of the population able to access the internet. BBC published an article about Eritrea’s censorship titled: “Eritrea – where ATMs are unknown, and Sim cards are like gold dust.” In a report published by Access Now in 2019, they state:
“Eritrea did not shut down mobile data because people are not allowed to use mobile internet anyway, even in the rare cases when they have SIM cards.”
Both governments have used telecommunication hacks to silence, suppress, intimidate, arrest, torture, and kill journalists, advocates, and activists. Eritrea is home to the most jailed journalists in Sub-Saharan Africa.
In 2012 the government hacked Radio Erena using a sophisticated Distributed Denial of Service (DDoS) attack, which kept the website down for three weeks. There have been other reports of Eritrean advocacy websites hacked in recent years. Eritrea shuts down numerous radio stations, independent news outlets, and schools that share critical views of their government.
Eritrean journalists, advocates, and human rights advocates have been intimidated, harassed, and silenced for far less. Eritrea can spy on its citizens as they are subjugated to outdated telecommunication services. We believe the Pegasus spyware was likely purchased to spy on individuals in their cabinet and GoE dissidents in the diaspora.
We offer our forensics support

Reclaim Eritrea is dedicating support to individuals concerned about targeting by Pegasus spyware. We run our forensic investigation using tools peer-reviewed by CitizenLab, shared with us by Amnesty International’s tech team. We’ll help you find traces of the spyware on both Apple and Android devices. Alternatively, iVerify is said to have a paid version of the forensics tool available in Apple’s iTunes store for $2.99.
You can fill out the form below if you’d like to be added to our forensics report mailing list, where we’ll share updates, instructions and provide additional support for tracing and remediating the malicious spyware on your device(s).